Citrix Receiver Adm Template
How to Deploy Citrix Receiver for Pass-Through Authentication Using. Will deploy Citrix Receiver to. Administrative Template should be.
Citrix recommends using the Group Policy Object icaclient.adm template file to configure rules for network routing, proxy servers, trusted server configuration, user routing, remote user devices, and the user experience. You can use the icaclient.adm template file with domain policies and local computer policies. For domain policies, import the template file using the Group Policy Management Console. This is especially useful for applying Receiver settings to a number of different user devices throughout the enterprise.

To affect a single user device, import the template file using the local Group Policy Editor on the device. To add or specify a store(s) via GPO:. As an administrator, open the Group Policy Editor by either running gpedit.msc locally from the Start menu when applying policies to a single computer, or by using the Group Policy Management Console when applying domain policies.
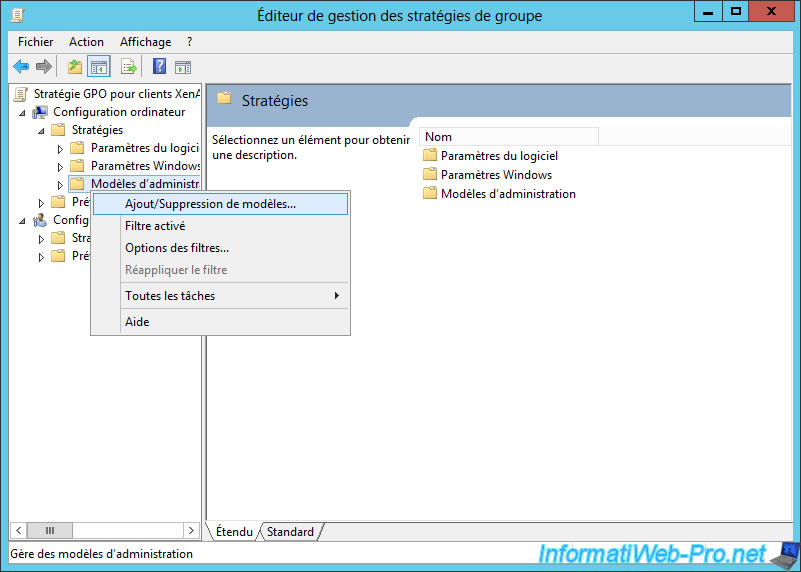
Note: If you already imported the icaclient template into the Group Policy Editor, you can leave out steps 2 to 5. In the left pane of the Group Policy Editor, select the Administrative Templates folder. From the Action menu, choose Add/Remove Templates. Choose Add and browse to the Configuration folder for Receiver (for 32-bit machines, usually C: Program Files Citrix ICA Client Configuration, for 64-bit machines usually C: Program Files (x86) Citrix ICA Client Configuration) and select icaclient.adm. Select Open to add the template and then Close to return to the Group Policy Editor. Under the Computer Configuration node, go to Administrative Templates Classic Administrative Templates (ADM) Citrix Components Citrix Receiver StoreFront, and select StoreFront Accounts List.
Edit the settings. Use the information in the next step to add or specifiy the accounts.
Enter a list of StoreFront accounts. For each entry, enter the following information, delimited by a semi-colon:.
Store name. The name that the user sees for this store. The url for the store. Store enabled state. Set to On or Off. Store description. The description that the user sees for this store.
Example: SalesStore;for Sales staff About ADMX Template Usage With the release of StoreFront 3.0 and Citrix Receiver 4.3, Citrix XenApp and XenDesktop support Microsoft’s new format for displaying registry-based policy settings using a standards-based XML file format, known as ADMX files. Note: More details can be found at this. On Windows Vista/ Windows Server 2008 and later, these new files replace ADM files, which used their own markup language. ADM files are still available for Windows XP Embedded platforms.
The administrative tools you use—the Group Policy Object Editor and the Group Policy Management Console—remain largely unchanged. In the majority of situations, you will not notice the presence of ADMX files during your day-to-day Group Policy administration tasks. One of the main benefits of using the new ADMX files is the central store. This option is available to you when you are administering domain-based GPOs, although the central store is not used by default. Unlike the case with ADM files earlier, the Group Policy Object Editor will not copy ADMX files to each edited GPO, but will provide the ability to read from either a single domain-level location on the domain controller sysvol (not user configurable) or from the local administrative workstation when the central store is unavailable.
You can share a custom ADMX file by copying the file to the central store, which makes it available automatically to all Group Policy administrators in a domain. This capability simplifies policy administration and improves storage optimization for GPO files. ADMX files are divided into language-neutral (ADMX) and language-specific (ADML) resources, available to all Group Policy administrators.
These factors allow Group Policy tools to adjust their UI according to the administrator's configured language. ADMX and ADML file names and locations The naming convention of the ADM files (provided in previous version of Receiver) has been improved. The table below provides the mapping of ADM files to their new ADMX file names: Citrix Receiver Version (prior to 4.3) Citrix Receiver version (4.3 and later) Icaclient.adm receiver.admx receiver.adm Icaclientusb.adm receiverusb.admx receiverusb.adm ica-file-signing.adm ica-file-signing.admx ica-file-signing.admx HdxFlash-Client.adm HdxFlash-Client.admx HdxFlash-Client.admx Note: Use.admx files on Windows Vista/Windows Server 2008 and later; use.adm files for other platforms. You can copy custom ADMX and ADML files distributed with Citrix Receiver installer to the central store, which makes it available automatically to all Group Policy administrators in a domain.
The table below provides the location where you need to copy the ADMX and ADML files: File type File location receiver.admx ICA Client Configuration ica-file-signing.admx ICA Client Configuration receiverusb.admx ICA Client Configuration en HdxFlash-Client.admx ICA Client Configuration receiver.adml ICA Client Configuration ica-file-signing.adml ICA Client Configuration receiverusb.adml ICA Client Configuration en HdxFlash-Client.adml ICA Client Configuration MUIculture Note: If Receiver is configured through VDA installation, ADMX/ADML files can be found in the installation directory. For example: online plugin Configuration. Receiver Configuration with Group Policy Object Template Citrix recommends using Group Policy Object template files to configure rules for the following Receiver features:. Client Engine. Customer Experience Improvement Program (CEIP). Diagnostics. Fast Connect API Support.
Citrix Receiver Adm
HDX MediaStream Flash Redirection - Client. ICA file signing. Multi-Stream ICA.
Network routing. Remoting for Generic USB and user devices. Self-service. Storefront. User authentication. User experience You can use template files to configure Local GPO and Domain-Based GPO. For details, see the Microsoft TechNet Library articles and.

Once the ADMX files are imported, Receiver related group policy settings can be found in the following locations:. Computer ConfigurationAdministrative TemplatesCitrix components. Computer ConfigurationAdministrative TemplatesHDX MediaStream Flash Redirection - Client. About TLS and Group Policies Use this policy to configure the TLS options that ensure Citrix Receiver securely identifies the server that it is connecting to and to encrypt all communication with the server. Citrix recommends that connections over untrusted networks use TLS. Citrix supports TLS 1.0, TLS 1.1 and TLS 1.2 protocols between Receiver and XenApp or XenDesktop. When this policy is enabled, you can force Receiver to use TLS for all connections to published applications and desktops by checking the 'Require SSL for all connections' checkbox.
Receiver identifies the server by the name on the security certificate that the server presents. This has the form of a DNS name (for example, www.citrix.com). You can restrict Receiver to connect only to particular servers specified by a comma separated list in the 'Allowed SSL servers' setting. Wildcards and port numbers can be specified here; for example,.citrix.com:4433 allows connection to any server whose common name ends with.citrix.com on port 4433. The accuracy of the information in a security certificate is asserted by the certificate's issuer. If Receiver does not recognize and trust a certificate's issuer, the connection is rejected.
When connecting by TLS the server may be configured to require Receiver to provide a security certificate identifying itself. Use the 'Client Authentication' setting to configure whether or not identification is provided automatically or if the user is notified. Options include:. never supply identification. only use the certificate configured here. to always prompt the user to select a certificate.
to prompt the user only if there a choice of certificate to supply Note: Use the 'Client Certificate' setting to specify the identifying certificate's thumbprint to avoid prompting the user unnecessarily. When verifying the server's security certificate, you can configure the plug-in to contact the certificate's issuer to obtain a Certificate Revocation List (CRL) to ensure that the server certificate has not been revoked. This enables a certificate to be invalidated by its issuer should a system be compromised. Use the “CRL verification setting” to configure the plug-in to:. not check CRLs at all. only check CRLs that have been previously obtained from the issuer.
actively retrieve an up-to-date CRL. to refuse to connect unless it can obtain an up-to-date CRL Organizations that configure TLS for a range of products can choose to identify servers intended for Citrix plug-ins by specifying a Certificate Policy OID as part of the security certificate. If a Policy OID is configured here, Receiver accepts only certificates that declare a compatible Policy. Some security policies have requirements related to the cryptographic algorithms used for a connection. You can restrict the plug-in to use only TLS v1.0, TLS 1.1 and TLS 1.2 with the 'TLS version' setting.
Similarly, you can restrict the plug-in to use only certain cryptographic ciphersuites. These cipersuites include: Government Ciphersuites:. TLSRSAWITHAES256CBCSHA. TLSRSAWITH3DESEDECBCSHA. TLSRSAWITHAES256GCMSHA384 Commercial Ciphersuites:. TLSRSAWITHAES128CBCSHA.
TLSRSAWITHRC4128SHA. TLSRSAWITHRC4128MD5. TLSRSAWITHAES128GCMSHA256.