Best Wifi Sniffers For Windows
Is a wifi sniffer for viewing Wi-Fi network information, channels, and packets on Microsoft Windows 10, 8.1, 8, 7 operating systems, and is also compatible with Windows 10. This has all the features of a Wi-Fi network scanner, displaying wireless network signal strength, channels, and behavior information, and it includes a Wi-Fi packet viewer to analyze network traffic. Let’s go over the steps on how to install and use the WiFi sniffer for Windows to monitor Wi-Fi network traffic: Install Wi-Fi sniffer on Windows The first step for using the Wi-Fi sniffer for Windows is to it from the product page to begin with the installation process. During the installation process, you will be prompted to install the monitor mode Wi-Fi packet capture driver. This functionality is necessary to view and capture all Wi-Fi network packets from nearby wireless networks.
5 free/low-cost Wi-Fi analyzers for Windows 10. By Eric Geier, Contributing Writer, Network World. If you’re looking for a free app, consider WiFi Analyzer. 20 Popular Wireless. Wi-Fi scanner for Microsoft Windows and OS X platforms. This tool was released under open source license and also awarded as “Best Open. Top 5 Wi-Fi Password Cracker Software for Windows 1. Packet sniffer and intrusion detection software for 802. Smartkey WiFi Password Recovery is the best.
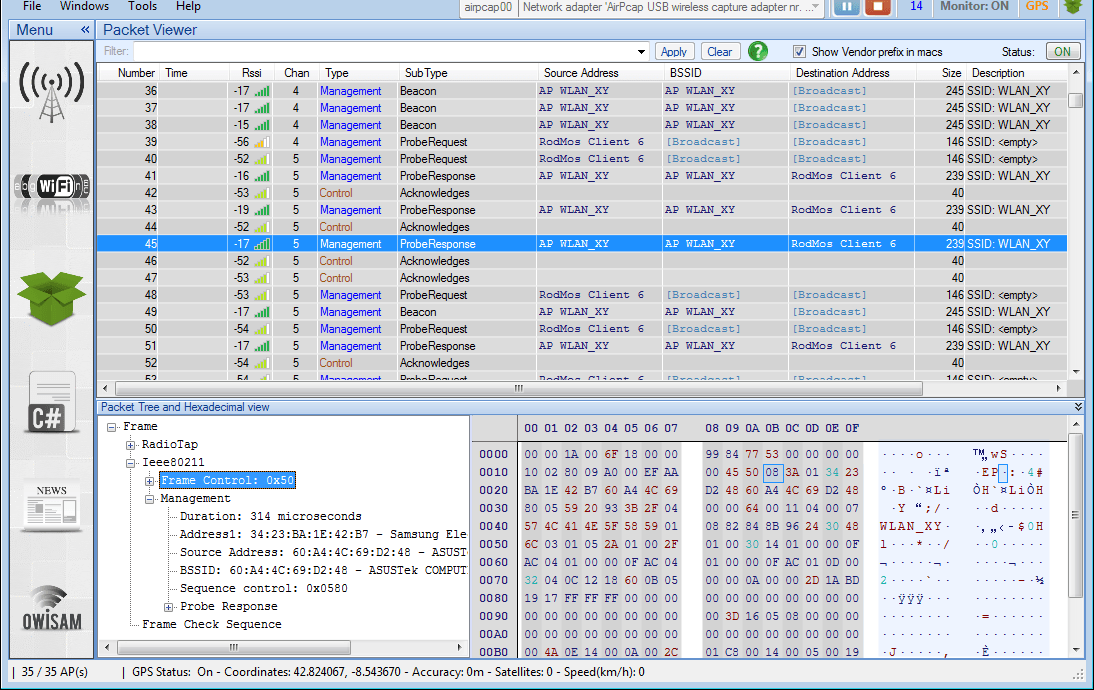
Bear in mind that this sniffer module requires a compatible wireless card, so make sure your and you have the latest Wi-Fi drivers installed in order to avoid system errors and clogging. If you have any doubts, do not install the Wi-Fi sniffer. Acrylic Wi-Fi is an Airpcap compatible software that allows you to use cards to capture Wi-Fi traffic from devices within reach. Wi-Fi network sniffer and Wi-Fi channel sniffer After starting Acrylic Wi-Fi as System Administrator, the three options for monitoring Wi-Fi network traffic will be enabled. The first two options are ideal for Wi-Fi channel analysis. Sniffer in normal mode: This mode uses Windows native Wi-Fi traffic capture mechanisms, so you will only be able to view Wi-Fi networks and channels. This mode does not require the installation of Acrylic’s Wi-Fi traffic capture drivers.
Sniffer in Wi-Fi monitor mode: This mode allows you to view all the clients connected to nearby Wi-Fi networks and devices. This mode does not allow you to be connected to a Wi-Fi network while the sniffer is capturing Wi-Fi network traffic and network and channel information, since your connection will be interrupted when changing between Wi-Fi channels and frequencies (2.4Ghz and 5Ghz). This mode is ideal for viewing 802.11 standard Wi-Fi threads within reach. Wi-Fi packet sniffer and Wi-Fi traffic sniffer The Wi-Fi packet sniffer functionality allows you to view the traffic of nearby Wi-Fi networks thanks to its integrated 802.11 standard traffic dissector.
This module allows you to apply visualization filters on wireless network traffic, view received Wi-Fi packet signal strength levels, and analyze network packet content. You can activate this mode while the sniffer is enabled by clicking on the Wi-Fi Packet button located at upper right area of the software interface, and it is used to view Wi-Fi network packets in real time or the packets saved to your local drive as. The Wi-Fi network packet sniffer module can be used on both normal and monitor modes, but it also supports a third option, the extended mode, for capturing the Wi-Fi network traffic generated by your equipment. The extended mode allows you to use the Wi-Fi network traffic sniffer while your wireless card is connected to a Wi-Fi network. Apart from viewing signaling packets (beacons, probe requests, probe responses, data packets, etc.), you will be able to view all the TCP, UDP, or Wi-Fi broadcast traffic generated by your system while connected. This way, you will be able to view and analyze all the web browsing ( HTTP) traffic, or any other network connection sent by the Wi-Fi network you are connected to. This capture mode does not allow you to view Wi-Fi traffic from other channels, since your wireless card is working at a fixed frequency.
The Wi-Fi network sniffer on extended mode and the network packet capture mode sectors are long-awaited new features on Acrylic Wi-Fi Professional v2.3, which is expected to be launched within the next few days. Download Wireless Network Sniffer for Windows 7/8/8.1/10 If you do not need to view Wi-Fi network packets or use a Wi-Fi network traffic sniffer, download, a free Wi-Fi network and channel sniffer for Windows that allows you to view all the wireless networks within reach. This version supports normal capture and monitor modes. If you need complete wireless network behavior information, Wi-Fi network sniffer is the right solution for you, since it supports all three Wi-Fi network capture modes, providing Wi-Fi network packet information in real time. A very useful tool for improving wireless network performance, detecting incidents, and learning more about Wi-Fi networking. Try it for free! And for advanced users, the Acrylic Wi-Fi driver allows you to.
We thought that this would be a good time to update this popular article, as new tools to hack private communications in WiFi hotspots are always evolving. This article discusses some of the most well-known WiFi hacking tools. Instructions Unfortunately, novice hackers don’t have to look very hard to find all they need to know regarding how to hack. For example:. Kali Linux is one of the best known hacking tool collections, and their provides many how-to hacking links. YouTube now has more than 300,000 videos on WiFi hacking, some with millions and millions of views.
One of the first listed is called “how to hack any WiFi hotspot in about 30 seconds.”. There are many other hacking websites out there, but since many of them are dubious and may have malware installed on them, we do not want to link to them as they may put you at risk.
Software The following is a list of the top 10 tools preferred by both ethical and black hat hackers in 2015:. Angry IP Scanner: Angry IP Scanner is a free network scanner that is very easy to use. It scans IP addresses and ports to find open ports. Burp Suite: A penetration testing tool that has several features that can map out the various pages and structure of a website by looking at cookies, and then initiates attacks on various web applications. Cain & Able: This is a multi-purpose tool that can intercept network traffic, using information contained in those packets to crack encrypted passwords using dictionary, brute-force and cryptanalysis attack methods, record VoIP conversations, recover wireless network keys, and analyze routing protocols. Its main purpose is the simplified recovery of passwords and credentials.
This software has been downloaded over 400,000 times. Ettercap: This widely used hacking tool works by placing a user’s network interface into promiscuous mode and by ARP poisoning, which is a process in which the hacker gives the wrong MAC or IP address to the network in order to carry out a Man-in-the-Middle attack.
John the Ripper: This hacking tool is popular for dictionary attack. It takes text string samples from a large dictionary, encrypts it in the same way as the password being crack, and then compares the output to the encrypted string. This is an example of a brute force attack. Metasploit: This hacking tool can be used for exploiting a network’s backdoor. While it’s not free, it is a huge popular penetration testing tool used by both ethical hackers, as well as unethical ones.
It helps provide information about known security vulnerabilities for a network. NMap: Also known as Network Mapper (or nmap for short), this free hacking tool is used by network administrators for security and auditing purposes.
Free Wifi Sniffers
It uses IP packets to determine what hosts are available on the networks, what services they offer, what types of protocols are being used, what operating systems are being used on the network, and what type of packet filters and firewalls are being used. Nessus Remote Security Scanner: This hacking tool can be used with client-server frameworks, and is the most popular vulnerability scanner worldwide. THC Hydra: This is another password hacking tool that uses a dictionary or brute force attack to try various password and login combinations against a log in page.
Wapiti: This is a penetration testing tool that is able to scan hundreds of possible vulnerabilities. It can audit the security of web application by performing black box scans, which scans the HTML pages of the application it is trying to attack in order to inject data.

For hackers that prefer a turn-key package, there are also hardware wireless hacking tools available. We’ve highlighted one called.
It’s a simple, small, portable device that can be carried into any hotspot and used to attract any laptop trying to find a WiFi access point. The Pineapple uses a technique called an Evil Twin attack. Hackers have used tools like KARMA to do the same thing for years, but with Pineapple, now you can buy a piece of hardware for only $100 that allows you to become a hacker without downloading or installing any software. Here’s what their website says: “Of course all of the Internet traffic flowing through the pineapple such as e-mail, instant messages and browser sessions are easily viewed or even modified by the pineapple holder.” Hacking Countermeasures Fortunately, there are resources that you can use to help combat these threats.
Below are two excellent books:. Hacking Exposed: Network Security Secrets & Solutions, by Joel Scambray.
This book talks about security from an offensive angle and includes a catalog of the weapons hackers use. Readers see what programs are out there, quickly understand what the programs can do, and benefit from detailed explanations of concepts that most system administrators do not understand in detail.
Hacking Exposed wastes no time in explaining how to implement the countermeasures that will render known attacks ineffective. Taking on the major network operating systems and network devices one at a time, the authors tell you exactly what UNIX configuration files to alter, what Windows NT Registry keys to change, and what settings to make in NetWare. Wi-Foo: The Secrets of Wireless Hacking, by A.
Vladimirov, K. Gavrilenko, and A. This book is the first practical and realistic book about 802.11 network penetration testing and hardening, based on a daily experience of breaking into and securing wireless LANs. Rather than collecting random wireless security news, tools, and methodologies, Wi-Foo presents a systematic approach to wireless security threats and countermeasures starting from the rational wireless hardware selection for security auditing and describes how to choose the optimal encryption ciphers for the particular network you are trying to protect. Definitions The following list includes common WiFi terms discussed in this white paper. For additional terms and definitions, please see our online. Brute Force Attack Brute force (also known as brute force cracking) is a trial and error method used by application programs to decode encrypted data such as passwords through exhaustive effort (using brute force) rather than employing intellectual strategies.
Just as a criminal might break into, or “crack” a safe by trying many possible combinations, a brute force cracking application proceeds through all possible combinations of legal characters in sequence. Brute force is considered to be an infallible, although time-consuming, approach. Encryption Encryption is the translation of data into a secret code.
To read encrypted data, you must have access to the secret key or password that was used to translate the data into cipher text. That same key or password enables you to decrypt cipher text back into the original plain text. Encryption is the most effective way to achieve data security, but depends on using keys known only by the sender and intended recipient. If a hacker can guess (crack) the key, data security is compromised. Evil Twin This is a rogue WiFi access point that appears to be a legitimate one, but actually has been set up by a hacker to intercept wireless communications. An Evil Twin is the wireless version of the “phishing” scam: an attacker fools wireless users into connecting their laptop or mobile phone by posing as a legitimate access point (such as a hotspot provider). When a victim connects to the Evil Twin, the hacker can launch man-in-the-middle attacks, listening in on all Internet traffic, or just ask for credit card information in the standard pay-for-access deal.
Tools for setting up an evil twin are easily available (e.g., Karma and Hotspotter). One recent study found that over 56% of laptops were broadcasting the name of their trusted WiFi networks, and that 34% of them were willing to connect to highly insecure WiFi networks – which could turn out to be Evil Twins. HTTPS Hypertext Transfer Protocol Secure (HTTPS) combines the Hypertext Transfer Protocol used by browsers and websites with the SSL/TLS protocol used to provide encrypted communication and web server authentication. HTTPS connections are often used to protect payment transactions on the Internet so that anyone that might intercept those packets cannot decipher sensitive information contained therein. Man-In-the-Middle Attacks A man-in-the-middle attack is a form of active eavesdropping in which the attacker makes independent connections a communication source and destination and relays messages between them, making those victims believe that they are talking directly to each other, when in fact the entire conversation is being controlled by the attacker. The attacker must be able to intercept all messages exchanged between the two victims. For example, an attacker within reception range of an unencrypted WiFi access point can insert himself as a man-in-the-middle by redirecting all packets through an Evil Twin.
Or an attacker can create a phishing website that poses as an online bank or merchant, letting victims sign into the phishing server over a SSL connection. The attacker can then log onto the real server using victim-supplied information, capturing all messages exchanged between the user and real server – for example, to steal credit card numbers. Sidejacking Sidejacking is a web attack method where a hacker uses packet sniffing to steal a session cookie from a website you just visited. These cookies are generally sent back to browsers unencrypted, even if the original website log-in was protected via HTTPS. Anyone listening can steal these cookies and then use them access your authenticated web session.
This recently made news because a programmer released a Firefox plug-in called Firesheep that makes it easy for an intruder sitting near you on an open network (like a public wifi hotspot) to sidejack many popular website sessions. For example, a sidejacker using Firesheep could take over your Facebook session, thereby gaining access to all of your sensitive data, and even send viral messages and wall posts to all of your friends. Sniffers Packet sniffers allow eavesdroppers to passively intercept data sent between your laptop or smartphone and other systems, such as web servers on the Internet. This is the easiest and most basic kind of wireless attack.
Any email, web search or file you transfer between computers or open from network locations on an unsecured wireless network can be captured by a nearby hacker using a sniffer. Sniffing tools are readily available for free on the web and there are at least 184 videos on YouTube to show budding hackers how to use them. The only way to protect yourself against WiFi sniffing in most public WiFi hotspots is to use a VPN to encrypt everything sent over the air. SSL A Netscape-defined protocol for securing data communications – particularly web transactions – sent across computer networks. The Secure Sockets Layer (SSL) protocol establishes a secure session by electronically authenticating the server end of any connection, and then using encryption to protect all subsequent transmissions.
The Transport Layer Security (TLS) protocol refers to the Internet standard replacement for SSL. Websites that are addressed by URLs that begin with https instead of http use SSL or TLS. WEP and WPA WEP and WPA are security protocols used to protect wireless networks. Wired Equivalent Privacy ( WEP) is a deprecated security protocol for IEEE 802.11 wireless networks. Because all wireless transmissions are susceptible to eavesdropping, WEP was introduced as part of the original 802.11 standard in 1997.
It was intended to provide confidentiality comparable to that of a traditional wired network. Since 2001, several serious weaknesses in the protocol have been identified so that today a WEP connection can be cracked within minutes. In response to these vulnerabilities, in 2003 the Wi-Fi Alliance announced that WEP had been superseded by Wi-Fi Protected Access (WPA). Wi-Fi Protected Access versions 1 and 2 ( WPA and WPA2) refer to certification programs that test WiFi product support for newer IEEE 802.11i standard security protocols that encrypt data sent over the air, from WiFi user to WiFi router. Why is it there are no countermeasures offered? I want a program that captures a hackers information or follows them back home, Maybe like what the railroads did to discourage spying on the telegraph lines.
They scheduled down time where high voltage would be run through the wires to destroy the coils of interception telegraph receiving sets. I have certainly wanted to plug my ethernet into the AC socket a time or two. I would be happy for a utility or a device that could reliably detect and log the IP address of every connection like caller ID does for phones. PITA to keep going to a whois. To discover its Google as usual. Andrew Lamb, If you plug your ethernet cable into the AC socket not only will you destroy the cable, but you will also destroy a bunch of networking equipment on the way to your ISP, as well as modems in neighbors houses depending on the amount of them, when a hacker is connected to your machine there is no direct wired connection between them and your computer, all you will accomplish is destroying your own stuff, As for logging IP addresses of connections, there is software that your router will send the connection information of every active connection and it will log it to your computer. It tells you source IP source port, end IP and end Port, as well as being configurable to try and resolve source hostname, IE if it comes from google.com.
The software does exist, you just have to know how to use it. The only reason sending HV down the telegraph lines in the olden days worked to destroy spying equipment connected is it was actually directly connected to the wire. Modern internet is very low voltage and works off a voltage differential. Because the only real countermeasure is actually securing your network. WEP is highly broken and using it these days is the equivalent of setting up a fancy shmancy 18th century lock in your front door. Sure it looks nice, but modern lock pickers are going to get around it in a matter of minutes. The real solution is: – DON’T USE WIFI.
Stop being a lazy ass and run up ethernet through your house. – If you really, REALLY need WiFi (say, roaming laptops or mobile devices) set it up with at least WPA2-AES/PSK as it is as of mid-2014 still safe.
Even WPA/TKIP or WPA2/TKIP are “secure” enough if you don’t have a guessable passphrase, but I wouldn’t count on that. Just skip through to AES.
How to.hack. and how to.defend against hacks.
involve the same knowledge. You have to know your enemy — how they think, how they operate — in order to stop them.
Most wars throughout history (in.any. culture) were won by espionage, by “intelligence” — not by brute force.
Why else do you think every major world power has spy agencies and elite hacker forces? The USAF (USA), IDF (Israel), and PLA (China), for example, have some of the world’s best hackers working for them — and often being.paid. to do it. Did you hear about that Anonymous take-down a while back, where several members were arrested on hacking charges? The FBI caught them because they had an informant in their ranks — a former member of Anonymous who was coerced into selling out his cohorts. You have to know how to do bad things in order to stop people from doing bad things. Ignorance is a weakness.
Now go learn you some hacking, and maybe you can stop people from hacking you, or your employer — unless you live in Germany, in which case even learning to hack is a crime (so don’t get caught). The longer your paswword the harder to crack there comes a point where an extra leter becomes hours, another few weeks, then years, then centuries, at least 20 should make the average cracker give up make it harder, buy having a few capital letters and numbers in it and symbols make it even harder, dont go over kill and make it a pain to remember keep it simple, just the longer the better if you can, change default ip of router set up static ip address on a diffrent subnet from dhcp dont broadcast ssid consider vpn+ddwrt.
Meh aPasswordLikeThisWithWpa2-PSKshouldsufice is not actually an effective password as all of that is in a dictionary and I could easily run my english dictionary through john the ripper to get through. Ip of your router does nothing, The cracking part to login just uses your signal and ip only matters after you been hacked (In which case all you do is look at your gateway ip and i have whatever ip you changed your router to) static ip address actually does not matter either because i could spoof my mac address to mimic yours and deauth you thus assuming your computers identity don’t broadcast ssid, many people assume that will help them yet when monitoring packets between the router and a communicating device the ssid is discovered by the packets.
Ddwrt is a firmware mod for your router (Just as easy as your standard router imo but does have fun local network features) and i don’t exactly know where you are trying to fit a virtual private network(VPN) in here as that does nothing as far as your actual wireless security goes. There are several definite ways to protect your network,;) research it and then you will know for sure what they are. The 2 secrets to success are 1. Don’t tell people everything you know and 2. Am for real he is legit i saw a post by one of his benefactor 4 days ago i decided to hook up hoping the outcome may either be one of these rippers but i told him i do’t give up front payment he replied by saying he do collect deposit before commencing any job and the balance be paid after the job, then i gave it a thought cause i don’t want to loose another sum to rippers after a while i paid him the deposit via bitcoin.
In less than 48 hours the job i ask him to do was delivered. Bro thank for not disappointing me, you can reach him through for a speedy work and prompt solution. HI everyone Am glad to bring to your notice the credibility of a reliable hacker that help me boost and erased my debt. He told me a week but completed the job in less than 3 days. Great dude when it comes to WhatsApp Hack, Facebook Hack and Phone Cloning, Background Check, Credit Boosting, Websites Hack and Cracking of Encrypted Files. Thanks for the nice job.
I feel everyone needing a hacker should hired his services. You can locate him via (universalhacker00 @ gmail. Com ) and get the best of hacking jobs. An hour ago Do you require any of the following services?.Hack Emails and Social Networks.Hack Mobile Phones and Service providers.Hack University grades and Transcripts.Clear Criminal and DMV records.Clear Debts, Mortgages.Fake IDs with authentic Social security numbers.Buy airline tickets for cheap.Security Breaches and Revenge Hacks.Search Engine Optimization.Security and Penetration testing.Loaded Credit Cards and western union hacks.Mt799, Bank wires and transfers.Money Laundering you should visit scientifichackerscrew at gmail. He is a fake hacker this is the email he will send and will, never do your service.
I have all the emails of our conversation., He even ask me to delete the bad comment. I want everybody to be aware.
Hacking into your partner’s phone is a very bold step to take because after getting what you have been searching it will make you sad if you get to see all your partner has been doing behind your back.I have been in this situation before and i was strong enough to get through with it and i don’t regret my decision to go through with.You have to be careful who you contact so you don’t fall into wrong hands.I got all i needed through someone i contacted you can contact him via email too with BLACKSPOTHACK @ gmailhe is very reliable!!! I have been through hard times with my spouse we fight almost everyday he always treats me like he doesn’t care and this was not the way we were living before, so i noticed something wasn’t right then i tried to break into his phone still i could not do that so i decided to look for a well experienced hacker then i came in contact with jeajamhacker @ gmail. Com who helped me break into his phone then i saw that the problem we have been having was as a results of a woman outside who my husband has been sleeping with and try to poison his mind about me.I cant thank you less (jeajamhacker) his services are cheap and affordable in case you need his help thank you.
Do you need a hacker to hire?Do you intend to change your school grades? Do you need to keep an eye on your spouse by gaining access to their email? As a parent do you want to know what your kids are up to on a daily basis on social media ie facebook, twitter, instagram, whatsapp, wechat and others to make sure they are not getting into trouble? Whatever it is ranging from Bank jobs, flipping cash, criminal records, DMV, Taxes and many more, he can help you get the job done, he is a professional hacker with over 6years+ experience. Contact.cyberlord231@gmail.com. CONTACT THEM FOR ALL KINDS OF HACKING JOB AT They are professional group hackers based in Europe,Asia,Africa.
Their services are 100% guaranteed so you have nothing to worry about, with their untraceable Penetration software. They offer the following services; -University grades changing -Bank accounts hack -Erase criminal records hack -Facebook hack -Twitters hack -email accounts hack -Grade Changes hack -Website crashed hack -server crashed hack.Skype hack -Databases hack -Word Press Blogs hack -Individual computers hack.Control devices remotely hack -Burner Numbers hack -Verified Paypal Accounts hack -Any social media account hack -Android & iPhone Hack -Text message interception hack -email interception hack – credit card for free online transactions -Sales of Blank Atm card and Credit card -Untraceable Ip etc.
Contact them at for more inquiry. The Most anonymous and discrete hack group you can trust. Our team of hackers, software developers and code breakers is the best in the world. With our team, nothing is impossible. Team work is the key, we get all your hack job done and delivered on time. Leave all your hack jobs in the hand of the professionals Only serious people should contact:QUICKHACKERTEAM at gmail dot c o m WE DO THE FOLLOWING -School grade/ transcript update -Phone monitoring(realtime and past records) -Social media/email realtime monitoring -Credit Score Increase -Erase Crime records from all server and security agency -Remove bad comments from online site. Hello, my husband has put a gps tracker on the car which he owns and he is using that for spying on me because I use that car too and whenever I go out of the house he is using the website gps live and keeping an eye on me all the time.
I believe that I’m having a right to know that too that there is a tracker fixed on the car. He tells me many times that he trusts me a lot and on the other side he is doing that. Whenever we arguing he says to me that I shall wait because very soon he will have a prove against me. He always knows where I stopped at the street and that makes me think about being tracked. I really don’t know what to do. I wish I could hand him over to the police because he is emotionally abusing me but I’m not sure if they will do that because he owns that car.
But I contacted the best hacker,reliable and trustworthy hacker with the help of CYBERHACKERWORLD002 AT GMAIL DOT COM I can spy,monitor and hack into all his conversation.